Introduction
Guardian Live provides a significant amount of information relating to the use of Guardian within a business. It provides information about individual Guardian systems (their performance, events that have been detected, and system health for example) as well as information about the people who interact with it (either receiving FIP calls, receiving reports or viewing the data that Guardian Live generates). As the data is ‘sensitive’ access needs to be considered within the context of a Data Privacy environment.
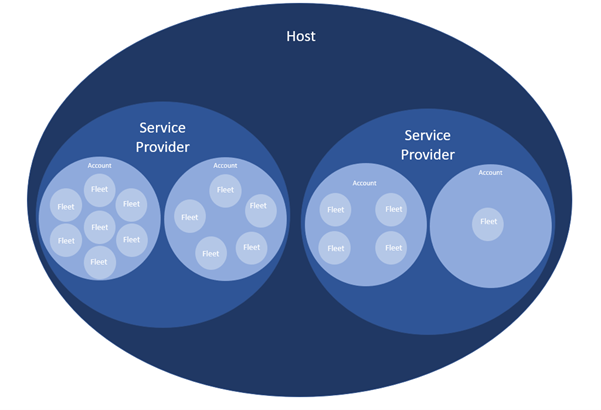
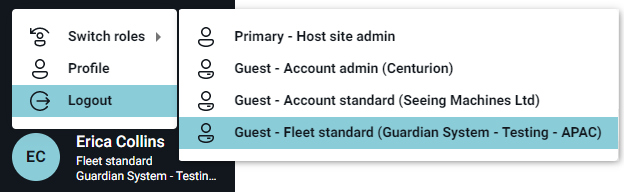
Your experience in Guardian Live will depend on the type of user you are. Guardian Live has been designed to provide access based on the business needs of the user. The need can be as simple as being a user who only needs to receive a phone call for a confirmed fatigue event, through to a user who is able to create and manage other users.
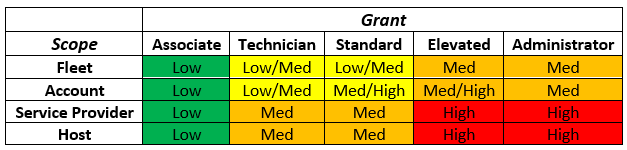
The different levels of access allow us to empower our Clients and Distributors to perform functions within a Data Privacy environment. The amount of information that a user can access or managed is a matrix, with the combination of Scope and Grant creating the amount of data privacy ‘risk’ that the user will pose to the business. An ‘Administrative’ user will be able to determine the Scope and Grants for users within their Scope.